可以在 runtime 下指令馬上更改 debug command,
# ipsec stroke loglevel ike 2
也可以寫在 ipsec.conf 內.
其他可以debug 的參數還有
types are dmn, mgr, ike, chd, job, cfg, knl, net, asn, enc, lib, esp, tls, tnc, imc, imv, pts and the level
is one of [-1, 0, 1, 2, 3, 4] (for silent, audit, control, controlmore, raw, private). By default, the level
is set to 1 for all types.
如果是要 decode ESP 封包, 要下 command
# ip xfrm state
src —.—.—.— dst —.—.—.—
proto esp spi 0xc5833fd7 reqid 4 mode tunnel
replay-window 32 flag af-unspec
auth-trunc hmac(sha1) 0xde33744975f816f9fdcb7969a3d5a337 96
enc cbc(aes) 0x9bf7b545ba3e35523c9a0c9f74b2c386ffb4634d
src —.—.—.— dst —.—.—.—
proto esp spi 0xc985f51a reqid 4 mode tunnel
replay-window 32 flag af-unspec
auth-trunc hmac(sha1) 0xf1341b4ddeb700925a8294264b271130 96
enc cbc(aes) 0x2f7a7dc8e136ed645d13b89fcd7b408fce3636ad
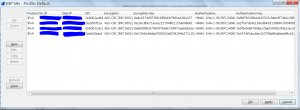
取出 SPI , encryption key and authentication key 填到 Wireshark ESP protocol 的 ESP SAs 內就可以了. 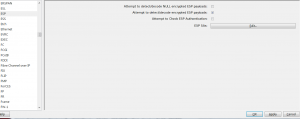





發佈留言